What are the risks organisations face in the world of digital security and privacy? We have spent several months exploring this; the answers are fascinating. Read on, to see cybersecurity in a new light.
Unravelling Risk Probabilities
Our mission began by asking a simple question: What are the most probable security and privacy risks for businesses, and how often do they occur annually? To answer this, we took insights from two major sources. The first, the UK Cyber Security Breaches Survey 2022, involves around 2,000 annual interviews with a variety of organisations. Our second guide was the data released by the UK Information Commissioner’s Office (ICO), which details serious security and privacy incidents.
Our analysis explored different types of cyber incident, like the scary "computers infected with ransomware". In the Breaches Survey, we focused on incidents where businesses reported losses. The ICO data gave us insights into both cyber-related and non-cyber issues.
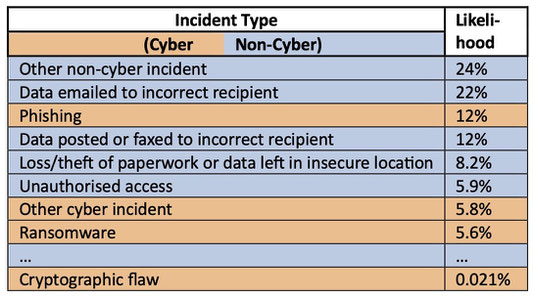
Next—and this is the technical part—we derived the likelihood of risks across both datasets. Essentially, we matched the risk categories from both sources, blending the data to give us an idea of the most probable risks. Some of our findings are colour-coded in Table 1, showing the most important risks, and differentiating between cyber and non-cyber incidents.
Of course, our approach isn't without its issues. The ideas of scaling all incidents based on cyber ones or assuming similarities among organisations might be contested. Plus, our results are UK-specific; the digital landscape can differ across borders. However, the objective risk data we provide is a pretty solid starting point.
We found two startling results: the range of probabilities was very different from what we'd expected; and that cyber risks, from people using hacking skills, were much smaller than we'd believed.
The Logarithmic Landscape of Risk
Our first eye-opener was that the probabilities of different risks don't increase in a straight line. Instead, they multiply! The likelihood of different types of risks is logarithmic (think of it as an accelerating curve) rather than linear. This isn't common knowledge in the cybersecurity sphere; probability scales are often shown as linear (though impact scales are usually logarithmic).
Our findings suggest that even our thinking about probabilities is logarithmic. Just as we perceive sound in octaves or the strength of earthquakes on the Richter scale, when we think of ‘low’, ‘medium’, or ‘high’ risk, it's not about percentages, but magnitudes. A high-risk scenario is vastly more probable than a medium one. This new lens can revolutionise how we approach risk assessment.
It’s Not Just a Cyber Issue
Another revelation was that non-cyber security and privacy concerns outweigh cyber ones in the UK. Take phishing, a common cyber threat. While damaging when it happens, it's outnumbered by issues like misdirected emails or other non-cyber incidents. Even old-school unauthorized access—people accessing systems they’re not supposed to—is more common than most kinds of cyber incident.
While technical bugs grab headlines, many more issues seem to arise from design or process faults. Ross Anderson's ground-breaking paper ‘Why Cryptosystems Fail’ noted that ATM thefts usually leveraged process or design loopholes instead of tech glitches. Similarly, a majority of security breaches have a human element, highlighting the importance of the user experience in security protocols.
Although software vulnerability problems are important, our findings suggest a broader perspective. Beyond just fixing vulnerabilities, adopting a holistic approach can lead to better security and privacy outcomes.
Conclusions
Security in the digital age isn't just about defending against hackers; it's about understanding a complex web of risks, both cyber and non-cyber. As we move forward in this digital era, we’ll need to adopt a comprehensive approach that combines technical, design, and human elements if we are to ensure a safer digital future for all.
So, keep checking for the non-cyber security and privacy risks in your system!
- Charles
Content © 2023 Charles Weir. Text munging support from ChatGPT4.